(Not so) Stupid Question 296: What are the pros and cons of excluding folders in Defender?
It was late and I was looking through my drafts of future ‘Tip of the Day!’ which I tweet out on daily basis. A colleague had mentioned to me that I could exclude certain folders to improve performance on my computer (at the time a slower computer) and I decided to make that the tip of the day as I recently had discovered that there were PowerShell cmdlets for that. I threw together an example, screenshotted it and tweeted it. This resulted in mixed reactions. The vast majority (that responded) responded positive, but a few not so much. Windows Defender is a built-in anti-virus protection in Windows 10, so excluding folders can lead to less protection. That was why some reacted with a hard stance against excluding folders. But on the other side some argued back and said it was worth it. I asked people to share the pros and cons and promised to share the resulting tweets in a blog post. This is the post.
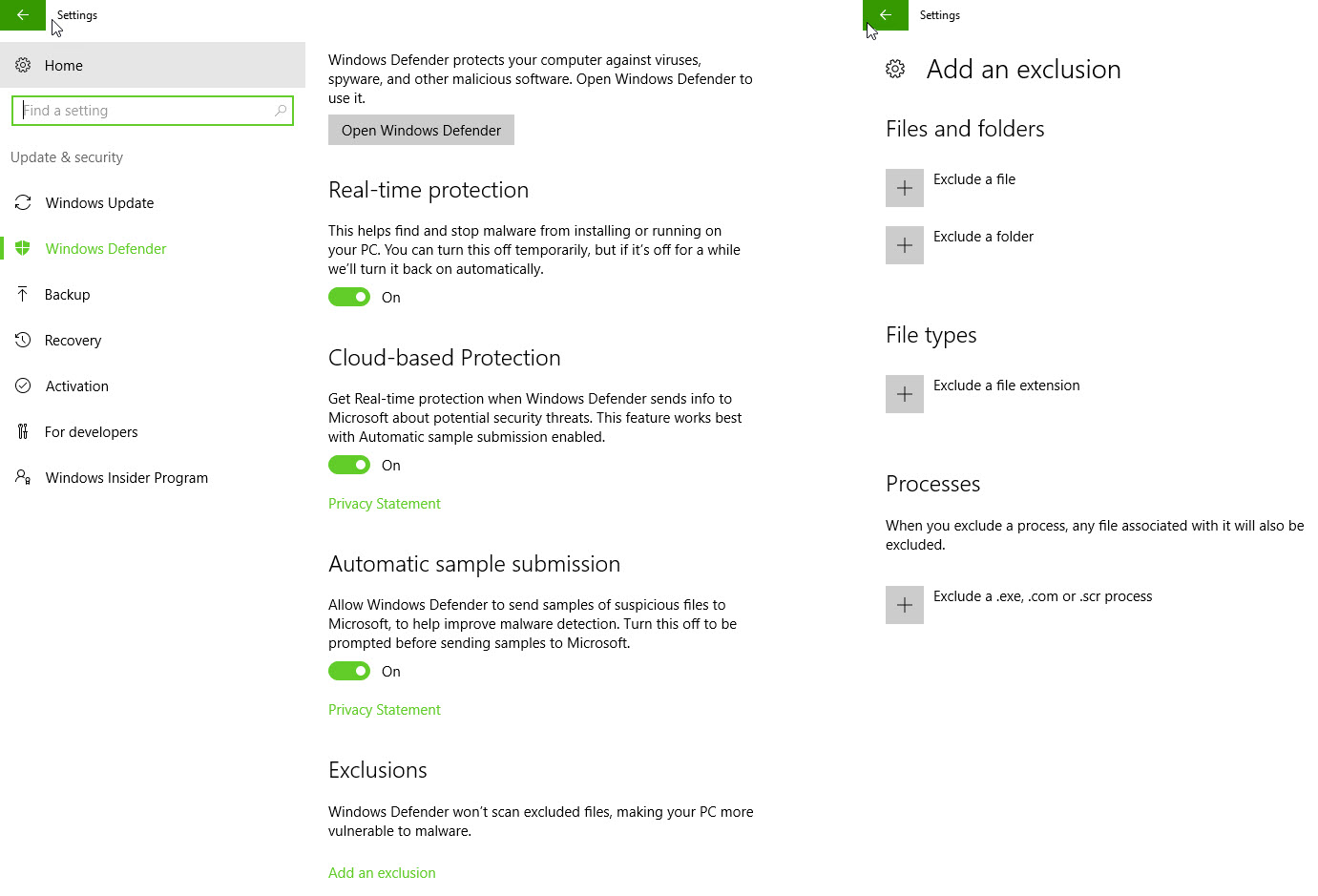
Summary of the discussion
There seems to be three camps, those that do it, those that only under certain circumstances reluctantly do it, and those that don’t. A supermini camp had to, it was SharePoint related and recommended (the tweet can be found in the tweet collection).
Those that argued against did so due to the increased risk of malware by leaving an opening and thus area for exposure. It was argued that the PowerShell modules would make it rather easy to find the vulnerable directories and files, - those can however be found by looking it up in the registry ( Stupid Question 114: What is the “Windows Registry”? )
More precisely, here: HKLM\SOFTWARE\Microsoft\Windows Defender\
The main argument for excluding folders, in particular those with many files, was performance. Although some questioned the validity of the argument as most of us use SSD’s now many commented back that the performance difference is noticeable regardless. The most common directories and files excluded were database and source code folders, in particular obj/bin. Besides that, Hyper-V related items and node modules, seemed to be a second favorite to exclude.
General advice was to, if you found it necessary to do so at all, exclude only folders and files that already had limited access or preferably were completely isolated. It seemed like many of those excluding folders (including me) were using other AV’s besides Defender. A small portion had decided to completely disable Defender.
Here is the discussion/ tweet collection. For privacy reasons names have not been added.
Me: Alright. Let’s have this discussion. Exclude folders in Defender or not? When is it ok, when is it a horrible idea?
I do for source code directories, REALLY slows compilation if you don’t.
Only OK when the folder itself is completely locked down from *anything* other than you being able to write to it. So, never.
Well I have a lot to say, you can disable scan on Read but not so sure about disabling on write for a folder, but it should be picked up in memory before writing to disk. With SSD and modern CPUs it should not be that much of an issue so don’t exclude folders. but deforestation based AV will never pick up all the bad things from the internet. You protect yourself the most by what you do.
good for database and code (increases performance), bad for downloads folder (increases risk)
I do exclude project build folders as an example only because I assign special permissions to those and use a certain account
Technical detail: Is it the source code folders or the bin/obj folders that will make it faster?
Exclude my source dirs as well as where some output binaries live/write data to
My thinking is that if it’s enough to disable it for bin/obj everything going in there is either scanned or your code
whenever you have workloads that are dependent on files being available for r/w so not locked by another process
years since I looked in detail but IIRC both - reading lots of little files is expensive for scanners.
depends on the function of the machine/vm/device. Isolated dev? Disable. Core banking app? Be very conservative
Ok when the risk is completely understood. So, never Ok for non-tech-savvy types.
but been doing it since before SSDs so the advantage is likely a lot less now (HDDs and small files…)
I’m in the camp who thinks virus scanners are useless anyway, so I’ll go for ‘OK always’ :)
if it speeds up my dev workflow it’s absolutely ok, IMO
well… I due the future to exclude the folder where I have my SVN checkouts. Would be a pain to scan them as I develop.
I exclude source and build folders. Makes a difference. Even on a super fast SSD.
maybe I don’t understand, but scanning, rescanning, resca… code files is just inefficient IMHO, have to trust SOME dirs.
I just use, avast free, windows firewall,
anytime it impacts my productivity, but within reason. I wouldn’t exclude the temp/dl folder, but source folders are fine.
IMHO - It’s OK for database files and database log files’ directories.
ike if people didn’t already have enough problems with malware. let’s improve performance at the cost of security once more.
seriously just remove the AV, setup an install script & reload the Dev system every few months. Reduces arbitrary “bugs” too.
disabled folders are stored in the registry. Thus, easy to read for malware. I do it anyway. Calculated risk.
there’s definitely situations that warrant folder exclusions. If you have a folder with a million tiny files, for example.
thing is, you won’t believe how many people actually exclude temp folders.
With some products like #SharePoint, excluding folders from scanning is pretty much mandatory: support.microsoft.com/en-ca/kb/952167 . Hence why I wanted to include ur automated exclusion tip as part of my OS build process for SP servers :)
I use Malwarebytes I hate defender or anything from Microsoft on Windows 10 basically
If developers started doing that en masse, exploiters would start targeting developers specifically. It’s a really bad idea
I find it very easy to get around defender anyway, so as long as the folder (1, not 50) is locked down & monitored, no biggie.
I think it’s always a horrible idea. It’s like poking a hole in a condom. You’re breaching your own security.
Don’t think I’ve ever added an exclusion, though I can imagine doing it for source folders as [] pointed out.
AV is something I’ve recently been working on, the choices you make can really impact when you have over 1k nodes.
if I’m doing my dev within a VM (which is most of the time) I go with YOLO mode [screenshot of excluding c dir]
done it for obj/bin folders before to speed up compilation
the problem is if you just whitelist a dir your increasing the attack surface
I excludes devenv.exe, source code folders (e.g. c:\projects), and all hyper-v related items.
I do exclude project build folders as an example only because I assign special permissions to those and use a certain account
temp is the first place I try dumping payloads
good for database and code (increases performance), bad for downloads folder (increases risk)
Only OK when the folder itself is completely locked down from *anything* other than you being able to write to it. So, never.
I do for source code directories, REALLY slows compilation if you don’t.
That is a stupid idea? Why exclude a folder? It would just become a breeding ground for viruses. #Derpey…[next tweet after asking for clarification] ..Yes, because if you exclude a folder from defender then people creating malware will just use that folder for storage, right?
Muhahaha. You don’t need to monitor temp. Not the malware directory you’re looking for. I can go about my business. Move along.
I couldn’t get myself to exclude anything. Malware can be anywhere on a system
Wouldn’t this be a hacker’s dream since they can do Get-MpPreference to see where to drop their malicious binaries?
For reference, these are the Windows Defender cmdlets:
|
Cmdlet |
| Description |
|---|
|
Add-MpPreference |
Modifies settings for Windows Defender. |
|
Get-MpComputerStatus |
Gets the status of antimalware software on the computer. |
|
Get-MpPreference |
Gets preferences for the Windows Defender scans and updates. |
|
Get-MpThreat |
Gets the history of threats detected on the computer. |
|
Get-MpThreatCatalog |
Gets known threats from the definitions catalog. |
|
Get-MpThreatDetection |
Gets active and past malware threats that Windows Defender detected. |
|
Remove-MpPreference |
Removes exclusions or default actions. |
|
Remove-MpThreat |
Removes active threats from a computer. |
|
Set-MpPreference |
Configures preferences for Windows Defender scans and updates. |
|
Start-MpScan |
Starts a scan on a computer. |
|
Start-MpWDOScan |
Starts a Windows Defender offline scan. |
|
Update-MpSignature |
Updates the antimalware definitions on a computer. |
Comments
Last modified on 2016-11-29
